Web Security Essentials: Shield Your Website from Cyber Threats and Defend Your Digital Presence!

In an increasingly interconnected digital world, where websites serve as the gateway to businesses, protecting your online presence has never been more crucial. From small e-commerce ventures to large corporate platforms, web security is a pressing concern that cannot be ignored. The rapid evolution of cyber threats demands a proactive approach to safeguarding websites from vulnerabilities that could compromise sensitive data, customer trust, and brand reputation.
In this era where websites have become the primary medium for conducting business, the consequences of inadequate web security can be devastating. Whether you’re running a small startup or managing a multinational corporation, every organization must equip itself with the knowledge and tools necessary to combat the ever-evolving landscape of cyber threats.
Consider, for a moment, the catastrophic impact of a successful cyber attack on your website. Sensitive customer data falls into the wrong hands, financial losses accrue, and the very reputation of your brand takes a severe blow. Such scenarios highlight the critical importance of implementing proactive web security measures that leave no room for vulnerabilities.
As technology advances and connectivity becomes more pervasive, the surface area for potential attacks expands. Malicious actors are constantly adapting their tactics, searching for weaknesses to exploit.
The State of Web Security:

In today’s interconnected digital landscape, web security has become a critical concern for website owners. The increasing number of cyber-attacks and data breaches highlight the importance of implementing robust security measures. Hackers are continuously seeking vulnerabilities in websites to exploit them for their malicious intent. These attacks can have severe consequences, including financial loss, reputation damage, legal liabilities, and loss of user trust.
Understanding Common Web Security Vulnerabilities:

a. Cross-Site Scripting (XSS):
i. Definition and Impact: Cross-Site Scripting (XSS) is a vulnerability that allows attackers to inject malicious scripts into web pages viewed by users. This vulnerability can lead to various harmful consequences, such as data theft, defacement of the website, or even browser hijacking. Attackers can exploit XSS vulnerabilities to steal sensitive user information, such as login credentials or financial data.
ii. Prevention Techniques: To mitigate XSS vulnerabilities, it is crucial to implement proper input sanitization and output encoding. Input sanitization involves filtering and validating user inputs to prevent the execution of malicious scripts. Output encoding ensures that any user-generated content displayed on web pages is properly encoded to prevent script execution. Additionally, implementing content security policies can help restrict the types of content that can be loaded and executed on a website.
b. SQL Injection:
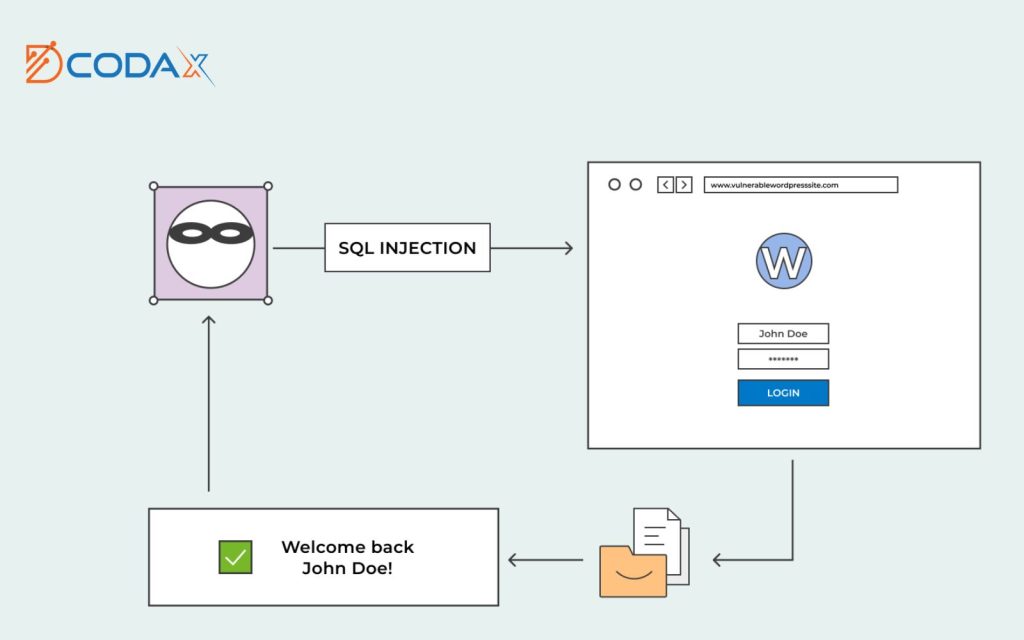
i. Definition and Impact: SQL injection is a web security vulnerability that occurs when attackers manipulate user inputs to execute unauthorized SQL queries. This vulnerability can lead to unauthorized access to databases, data manipulation, and potential server compromise. Attackers can use SQL injection to extract sensitive information, modify data, or even gain administrative privileges.
ii. Prevention Techniques: To protect against SQL injection attacks, it is essential to use parameterized queries or prepared statements when interacting with databases. Parameterized queries separate user input from the SQL query, preventing malicious code injection. Input validation should also be performed to ensure that user inputs conform to expected formats and types. Additionally, strict database permissions should be enforced to limit the potential impact of successful SQL injection attacks.
The Power of Input Validation:

Input validation is a fundamental practice for securing websites. It involves verifying and sanitizing user inputs to ensure they meet the expected criteria. By implementing robust input validation techniques, website owners can significantly reduce the risk of vulnerabilities caused by malicious inputs.
Effective input validation includes the following steps:
a. Sanitization:
User inputs should be sanitized to remove potentially harmful characters or scripts. This can be achieved by implementing input filters or using security libraries that handle input sanitization.
b. Data Type Validation:
Inputs should be validated to ensure they match the expected data types, such as numbers, email addresses, or dates. This helps prevent unexpected behavior or vulnerabilities caused by incorrect data handling.
c. Length and Format Restrictions:
Setting limits on input length and enforcing specific formats (e.g., for passwords or credit card numbers) helps prevent input-related vulnerabilities, such as buffer overflows or injection attacks.
It is essential to implement both client-side and server-side validation. Client-side validation provides immediate feedback to users, enhancing the user experience. However, server-side validation is crucial as client-side validation can be bypassed by attackers.
Secure Authentication:

Authentication is the process of verifying the identity of users accessing a website. Implementing secure authentication mechanisms is vital to prevent unauthorized access and protect user accounts.
a. Password Policies:
Implementing strong password policies helps ensure that user accounts are adequately protected. This includes requirements for password complexity (e.g., a combination of uppercase and lowercase letters, numbers, and special characters), enforcing a minimum password length, and prohibiting commonly used passwords. Password hashing algorithms should be used to store passwords securely.
b. Multi-Factor Authentication (MFA):

Multi-factor authentication adds an additional layer of security by requiring users to provide multiple pieces of evidence to verify their identity. This can include something the user knows (e.g., a password), something the user possesses (e.g., a physical token or smartphone), or something unique to the user (e.g., biometrics). Implementing MFA significantly reduces the risk of unauthorized access, even if passwords are compromised.
c. Account Lockouts and Brute Force Protection:
Implementing account lockouts after a certain number of failed login attempts can prevent brute force attacks, where attackers try various combinations of usernames and passwords to gain unauthorized access. Additionally, implementing CAPTCHAs and IP blocking can further protect against brute force attacks and other malicious activities.
Effective Session Management:

Session management is crucial for maintaining secure and trusted user sessions on a website. Proper session management techniques help prevent session hijacking, session fixation, and other session-related vulnerabilities.
a. Session Tokens:
Secure session token generation is essential to prevent attackers from predicting or stealing session identifiers. Session tokens should be long, random, and unique for each user session. Furthermore, session tokens should be transmitted securely using HTTPS, and their exposure should be minimized by setting HTTP-only and secure flags for session cookies.
b. Session Expiration and Invalidation:
Setting appropriate session expiration times helps limit the duration of active sessions, reducing the risk of unauthorized access. Sessions should also be invalidated upon user logout or after a period of inactivity. Proper session invalidation ensures that even if an attacker obtains a session token, it becomes useless after its expiration or when the user logs out.
c. Cross-Site Request Forgery (CSRF) Prevention:

Cross-Site Request Forgery (CSRF) attacks occur when attackers trick users into performing unintended actions on websites they are authenticated to. Implementing protective measures such as using anti-CSRF tokens and validating the origin of requests helps mitigate the risk of CSRF attacks.
Regular Security Audits and Updates:
Web security is an ongoing process that requires regular security audits and staying up-to-date with the latest patches and security updates. Websites should be periodically audited to identify vulnerabilities and weaknesses. Vulnerability scans and penetration testing can help identify and rectify potential security flaws. It is crucial to keep website platforms, frameworks, and plugins updated to benefit from security patches and bug fixes.
Educating Website Users:
User awareness plays a crucial role in maintaining web security. Educating users about common threats, good password hygiene, and safe browsing practices can significantly reduce the risk of successful attacks. Regularly reminding users to avoid suspicious links and downloads, use strong passwords, and enable MFA can greatly enhance overall web security.
Wrapping it up
Web security is a critical aspect of running a successful and trustworthy website. By understanding common vulnerabilities like XSS and SQL injection and implementing the essential techniques discussed in this article, website owners can fortify their digital assets against cyber threats. Remember, web security is an ongoing process that requires constant vigilance, regular audits, and proactive measures to stay one step ahead of malicious actors. With the right mindset and the implementation of these web security essentials, you can ensure the safety and integrity of your website and provide a secure online experience for your users.
About us
In today’s interconnected digital world, ensuring robust web security is paramount to protect your website from cyber threats and defend your valuable digital presence. At Dcodax, we prioritize web security and offer essential measures to shield your website from potential attacks.
Our comprehensive web security solutions encompass multiple layers of defense. We begin by implementing secure authentication and access control mechanisms to ensure that only authorized individuals can access your website’s sensitive data and functionalities. Additionally, we employ industry-standard encryption protocols to safeguard data transmission and protect sensitive information from unauthorized access.
To maintain the highest level of security, our team conducts regular security audits and vulnerability assessments to identify and address any potential weaknesses in your website’s infrastructure. We also utilize advanced monitoring systems to detect and mitigate security threats in real time, minimizing the risk of breaches and data compromises.
At Dcodax, we stay up-to-date with the latest security practices and technologies, utilizing robust firewalls, intrusion detection systems, and advanced malware protection mechanisms to fortify your website’s security perimeter. In the event of a security incident, our experienced team is ready to respond swiftly and effectively, ensuring minimal impact and restoring the integrity of your website.
Choose Dcodax as your trusted web security partner to shield your website from cyber threats and defend your digital presence. With our web security essentials in place, you can focus on your core business with confidence, knowing that your valuable online assets are well-protected.
With Dcodax by your side, the sky’s the limit!
For Any Type of Free Consultancy, Dcodax is Always Available for your Help.
For more; Contact Us Now